My kid like many out there has met and fallen in love with Minecraft. Everyday I hear about what him and his friends were dreaming up of building while they should have been paying attention in school. He want's to play on a server with his buddies but i'm not about to open our network up to the world and of course he doesn't understand this. So with Google's announcement about cloud and lower prices earlier in the week I thought I could try out Google Compute Engine and help my kid and his buddies have a safe place to play Minecraft together at the same time. The first thing I did was look for a guide online. There are several out there for AWS and Azure but I couldn't find any for Google Compute Engine so I figured I would make one.. so here we go. A little disclaimer before we get started. First, I am Linux savvy but know next to nothing about Minecraft, so this is a completely vanilla load and if anyone wants to post a question in the comments it's unlikely I'll be able to help with any that are Minecraft related. Second, I'm not perfect, I tried to be thorough with notes and screenshots as I went through the process but it's possible I missed one or two, and there may be typos. You are warned!.
Step 1. login to google developers Console
login to google developers Console at https://cloud.google.com/
If you don't already have a Google account you'll need to make one first, but you probably do.
Step 2. Create a new project
Click create a new project and give it whatever project name you want.
Click on the project and then click on Compute Engine
It will prompt you to enable billing
Confirm your Country and then fill out your billing information
Click submit
Step 3. Create your VM instance
Click on new instance
Select your server settings. I chose the following:
Machine Type> high cpu 2 core 1.8 G mem .08 cents / hour
boot source > new persistent disk from image
image > debian 7 image
Leave all other options default and hit create
Step 3. Install cygwin for windows
Download cygwin at http://cygwin.com/install.html
Download and install the 32 bit version for windows (the 64 bit has a bug apparently) http://cygwin.com/setup-x86.exe
Run the executable and start the installer
Choose all the default settings
Choose a download mirror
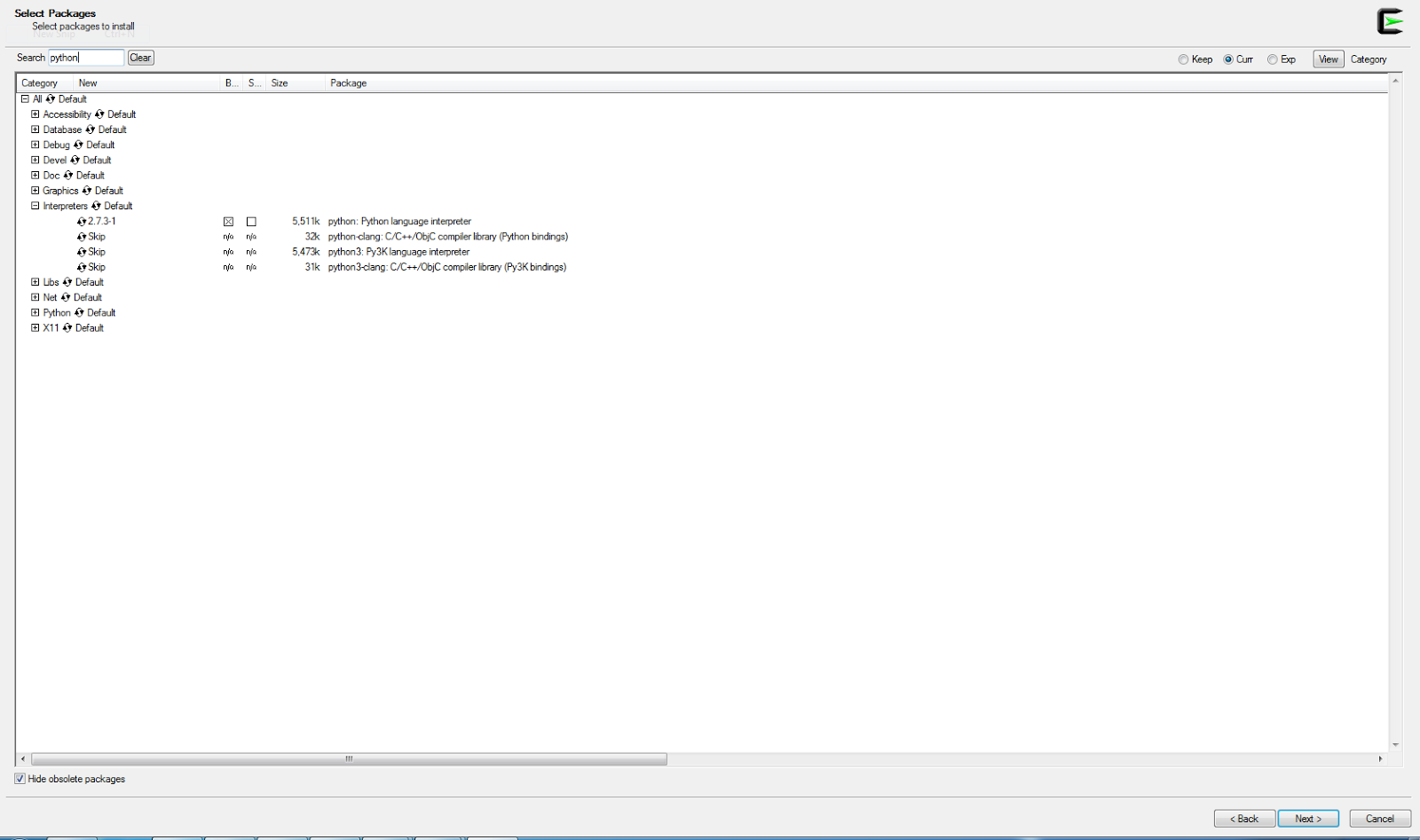
When installing Cygwin, be sure to select openssh, curl, and the latest 2.6.x or 2.7.x version of python from the package selection screen.
I'll make the next screenshots bigger because the text is really small...
Selecting openssh
Selecting Curl
Selecting python
(At this point I was thinking "why can’t I just ssh in from my browser or get a console screen?" but whatever I guess..)
Click next a few time and finally click finish
Step 4. Install Google Cloud SDK
In windows run start>programs>cygwin>terminal
In the terminal run (or copy and paste)
curl https://dl.google.com/dl/cloudsdk/release/install_google_cloud_sdk.bash | bash
Select y and accept defaults, when it completes, close and reopen the cygwin terminal
In the terminal run (or copy and paste) gcloud auth login
Paste the url it creates into your browser and hit accept at the Google screen
Get the code the website generates and past it back into your terminal
When it asks for your project ID get it from your Google Developers Console
Step 5. Log into your VM
In your cygwin terminal run
$ gcutil --project=YOURPROJECTID ssh YOURVMNAME (this is how you will log into your VM from now on)
Enter pass phrase if you want to set up a password for your ssh keys
Ok, now your logged in
Step 6. Install Java
In your terminal (you should be logged into your VM at this point) run
sudo su -
apt-get install openjdk-7-jre
Hit 'y' or accept for any questions it asks you. This will download and install Java which is required for running minecraft
exit (run exit only once or you'll have to log back into your VM)
Step 7. Install Minecraft
In your terminal (still logged into your VM) run the following commands
mkdir minecraft (makes a minecraft directory)
cd minecraft (moves you into the minecraft directory)
wget https://s3.amazonaws.com/Minecraft.Download/versions/1.7.5/minecraft_server.1.7.5.jar (downloads the minecraft jar file)
java -jar minecraft_server.jar nogui (starts the minecraft server)
Once you run the java command you should see alot of text pop up about starting worlds and listening on port *.25565, etc, and finally you'll start to see console output from the server.
Step 8. Create firewall rule
Although you get a public IP address with your VM it only allow connections from the outside world on port 22 (ssh) so you'll need to add a new firewall rule.
In the developers console click on your vm then Compute Engine and then Networks.
Under firewall rules click new rule and enter the information for your server. Basically just give the rule a name and under ports and protocols put tcp:25565 or whatever port your minecraft server is listening on (it shows you when you start the server (step 7))
Click create to save the setting
Step 8. Add the new server to your Minecraft list of multiplayer worlds
To get your VM IP click on the VM in Compute Engine under your project in the Google Developers Console. Under the usage statistics it should show your external IP. This is the IP you add into Minecraft and the IP you give your friends.
If all goes well you should connect to your Minecraft server and be able to start playing.
Afterthoughts:
If you've read this far you have some patience which you'll need to use Google's Compute Engine. It doesn't really seem to be made for everyday people just trying to run a server for their kid to play minecraft on, but it does work and very well too. That being said there's a few things you should know.
1. You can't turn your server off and leave it off. You can do a restart on it, but if you give it a shut down only command (i.e. shutdown, poweroff, init 0) it will go into a terminated state. (I learned the hard way) If this happens you'll have to delete the VM (but don't delete your persistent disk) and make a new instance an which point you can reattach the disk that already has Minecraft on it.
2. This is probably more difficult than running on AWS, and maybe more so than azure. Mainly because on windows you don't have a terminal and so you need cygwin and Google Cloud SDK. They should really build a way to log in via the developer console.
3. Unless your kid plays Minecraft most days of the week, or you want to let their friends play even when your kid isn't playing this isn't really cost effective. Leaving the machine running 24/7 will be about 40 bucks a month with the type of server I created. That's alot to pay every month for Minecraft. If they only play on the weekends though it isn't so bad as you can shutdown and delete the instance on Sunday night and restart it on Friday after school and this will save you alot of money. It will be more difficult though because you'll be recreating the VM every week and possibly updating the IP address for yourself and your kids friends.
All in all it was a fun experience to try and it does work so hopefully someone else will be able to try it too now.
If you have any questions leave them at the bottom and maybe I can help you out.
Unix Admin Online
Thursday, March 27, 2014
Tuesday, March 27, 2012
Chroot dns/named/bind in Solaris 10 zone
My latest project was to create a chroot bind environment inside a solaris 10 zone. The goal is to make it as secure as possible since it will be on an outside facing network. Here's the guide.
-->
-->
To configure a Secure dns instance in a
Solaris 10 non-global zone using zfs, roles, and chroot:
- Create the zone and filesystem for the dns chroot structure
* This assumes that
you have a zfs root or at least a zfs pool to build your zone on
- zfs create rpool/Root/S10x_u9/zone1
- chmod 700 /zone1
- zonecfg -z zone1
zonecfg:zone1>
create
zonecfg:zone1>
set zonepath=/zone1
zonecfg:zone1>
set autoboot=true
zonecfg:zone1>
add net
zonecfg:zone1:net>
set physical=net0
* giving the zone
a physical interface instead of an ip makes enables an exclusive ip
zone. This gives the benefit of having a physically separated
interface that can be on a network not connected to the global zone.
zonecfg:zone1:net>
end
zonecfg:zone1>
set ip-type=exclusive
zonecfg:zone1>
verify
zonecfg:zone1>
commit
zonecfg:zone1>
exit
*you can now run a
# zoneadm list -civ to see the zone as configured
- zoneadm -z zone1 install
- zoneadm -z zone1 boot
- zlogin -C -e “#.” zone1
*Login on the
console for the zone to se the original parameters, just like an
initial install of Solaris. (~.) is the escape sequence although this
functionality is lacking. That's why I add the -e “#.” to the
zlogin command. This way I wont get kicked out of the entire session.
It may be necessary to log back into the global zone and kill the
zlogin -C process.
- Create the role and modify the dns services to run as a role and in a chroot environment
* These commands
are ran in the zone unless otherwise noted
- roleadd -d /local/dns -s /bin/false named
* make the role,
give it a home dir of the chroot filesystem and set the shell to
/bin/false
- groupadd dnsgroup
- rolemod -g dnsgroup named
- chown -R named:dnsgroup /local/dns
- cd /var/svc/manifest/network/dns
- cp server.xml chroot-server.xml
- vi chroot-server.xml
*Make the
following changes
- go down to last dependency statement and copy 7 line (7yy)
- go just above the <exec_method> statement and paste your seven line (p)
- change the dependency statement as follows
<dependency
name='config'
grouping='optional_all'
restart_on='error'
type='path'>
<service_fmri
value='file://localhost/local/dns/etc/named.conf'
/>
</dependency>
* modify this line
if your named.conf is not going to be under an etc directory in your
chroot structure
- change the instance name statement to reflect the name of your new server chroot-server
* the line looks like
this
<instance
name='chroot-server' enabled='false' >
- go down to the method credential statement and change the user and group to our role and group
<method_credential
user='named'
group='dnsgroup'
* leave the rest of
the statement alone
- change the propval method for chroot_dir
<propval
name='chroot_dir' type='astring' value='/local/dns' />
- validate the configured
svccfg validate
chroot-server.xml
*if there are any
errors go back and fix whichever line it is complaining about
- import the service
- svccfg
- svc:> import /var/svc/manifest/network/dns/chroot-server.xml
- svc:> exit
- Configure your dns files within the chroot directory structure
* Typically you
will want to put your dns files in standard as possible locations
inside your chroot directory structure of /local/dns. For instance
usual directories will be etc, var, and db. Another directory we will
need to create under /local/dns is dev. This will hold our character
devices used by dns.
- mkdir /local/dns/etc
- mkdir /local/dns/var
- mkdir /local/dns/db
- mkdir /local/dns/dev
*The devices
necessary for named will need to added to this dev directory. Because
this is in a zone this will have be done from the global zone.
- ls -laL /dev/poll
- ls -laL /dev/random
- ls -laL /dev/urandom
*Be sure to not
the major and minor number and the type of device for each of these
files.
For instance ls
-laL /dev/poll produces
crw-rw-rw 1 root
sys 135, 0 /dev/poll
The “c” means
a character device and the first number (135) is the major and the
second (0) is the minor
- Add the devices to the zone
*Done from the
global zone
- mknod /zone1/root/local/dns/dev/poll c 135 0
- mknod /zone1/root/local/dns/dev/random c 149 0
- mknod /zone1/root/local/dns/dev/urandom c 149 1
- Make the named user and dnsgroup owner of the devices
- chown -R named:dnsgroup /local/dns/dev
- Configure your dns files however you see fit. The only things to keep in mind is that all files needed to run dns including logs and pid files will need to exist with your /local/dns chroot directory structure. Also the named.conf needs to exist in the location you specified while creating the chroot-server.xml service.
- Modify the named.conf file to point to files within the directory structure.
*All paths in the
named.conf should be relative to the chroot starting point. For
instance the directory option should read /db, not /local/dns/db.
Here are the changes I make in named.conf.
- Directory “/db”;
- key-directory “/etc/”;
- pid-file “/etc/named.pid”;
*The main point is
that any file or path specified in the named.conf needs to be
relative the the chroot starting point of /local/dns so if you keep
key files in /local/dns/key/zone1.key the entry in the named.conf
should only point to /key/zone1.key
- Enable the dns service
- svcadm enable svc:/network/dns/server:chroot-server
*ps -ef | grep
named
the named process
should be running with a “-t” option and the path to the chroot
directory structure. If not look in /var/adm/messages for any errors
(usually due to permissions of the devices or non-chroot based file
paths in the named.conf
References:
Subscribe to:
Comments (Atom)